|
There are no user reviews for ServerPronto.
|
ServerPronto is a dedicated hosting subsidiary of Infolink, one of a few profitable Data Center Corporations in the world. From it's beginning in January 1999, Infolink served the "Value Orientated" segment of the Internet market. Not by offering a sub-standard product at a low price, but by offering a top-quality, feature rich product at an incredible price. Since the beginning Infolink has enjoyed dramatic growth while other's in the industry have suffered. We operate our own network in the USA and maintain redundant Fiber Optic Rings which allow us to directly peer with Tier 1 Internet Backbones.
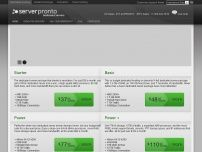
56 Dedicated hosting packages
($49.95 - $274.95)
16 Cloud hosting packages
($14.95 - $374.95)
Company Info:
Site Info:
Contact Info:
User Reviews:
There are no user reviews for ServerPronto.
Blog posts
Recent posts from
ServerPronto blog:
Dec 02, 2015
In a time where many servers are delivered faster than pizzas, many never stop to consider the risks and problems that arise with instant and near instant server provisioning times. Most server hosts want to keep it this way too! The promise of a quick delivery is attractive, but server hosts will never tell you […]
Dec 01, 2015
Servers are good examples of a form of technology that will most likely never be replaced. As long as cyberspace exists, we need a place to house it. Instead of ever going away, servers will instead simply continue to evolve. The natural question, then, is what is the future of servers? Where will they finally […]
Nov 30, 2015
If you depend on a hosting service, you need them to be worth every penny. The following are signs they may not be holding up their end of the bargain. Uptime No hosting company can ever guarantee 100% uptime, but they should get as close as possible. Uptime refers to how much of the time […]
Nov 29, 2015
Hosting is too important to stick with a provider that isn’t pulling their weight. However, as you have probably learned, changing hosting companies isn’t necessarily an easy thing to do. No matter what your reason, you need to take certain steps before cancelling your account. Guide to Changing Web Hosting Companies ? Begin by backing […]
Nov 28, 2015
Every company needs a server to host their website. However, many people are confused about what kinds of options exist. To help you make sense of them all, let’s take a look at the three main types that are out there. Shared Hosting Is an Apartment Shared hosting is like living in an apartment. For […]
Nov 27, 2015
When you consider just how important a company’s web presence is for all of their digital offerings, it’s easy to contend that one of the most vital components of their entire operation is their server. This is an easy element to take for granted, but the moment it stops working as you need it to, […]
Nov 25, 2015
Everyone knows that dedicated servers are preferable over the shared option. It’s like comparing a home to an apartment or your own car to the city bus. However, a lot of people are caught on the fence when trying to decide between the two. If you don’t get the kind of traffic that necessitates a […]
Nov 24, 2015
If you’re like most people, you’ve probably considered investing in a dedicated server for your company on more than a few occasions. However, like so many, the discussion probably stopped short when you got to the actual cost. There’s no doubt about it, the cost of a dedicated server is definitely going to put more […]
Nov 23, 2015
Most people nowadays understand that dedicated servers are preferable to any other option you might be thinking of. Even if you don’t opt for virtualization right now, having a dedicated server is going to give you the best possible result for your website or whatever else you need hosting for. In the Game Industry, Dedicated […]
Nov 20, 2015
If you’re a gamer, most likely, you’re one of the millions who take this hobby extremely seriously. Today’s gamers love their favorite pastime to the point that many have actually made careers out of them. This may not be to the extent you’ve taken it—or even hope to—but that doesn’t mean you don’t want to […]
Nov 19, 2015
Server virtualization is the next big trend you can expect to see more and more of in the future. Having a dedicated server is great, but having that data available in a virtual environment is just an unrivaled benefit. However, if you’re currently stuck at the actual virtualization process, then you may want to think […]
Nov 18, 2015
First, consider your home Internet. While it shouldn’t be a problem for most, you’d hate to find out that your Internet connection can’t handle adding a server to it. However, as long as you have a 25 Mbps download/10 Mbps uplink, you shouldn’t have too much trouble in this important regard. That’s if, of course, […]
Nov 17, 2015
Whether it’s finally time to invest in a server or you’re upgrading from a prior version, it would make sense that your decision would come down to a dedicated server and cloud hosting. Before you pick, though, let’s make sense of both options as best as possible. Cloud Server Hosting Let’s begin by looking at […]
Nov 16, 2015
P2V stands for physical to virtual, which is why you’ll so often see the word “migration” right behind this acronym. It refers to the process of migrating an OS (operating system) application program and data from your system’s main hard disk over to a virtual machine. Why is Physical to Virtual Migration Such a Big […]
Nov 15, 2015
The benefits of having a dedicated server are well-documented at this point. Everyone knows there are countless reasons to utilize this kind of digital asset. Unfortunately, many malicious parties out there are equally excited about your new server too. That’s because, if you don’t take steps to protect it, you’re consolidating a lot of valuable […]
Nov 14, 2015
If you’re in the market for server space, chances are you have probably already heard about the dedicated option. To put it simply for those of you who aren’t familiar with it, you can pay to have you own dedicated server, one that will be for your use and your use only, but largely managed […]
Nov 13, 2015
By now, most people who need a server understand that going with a dedicated server would be their best option. It’s like having your own house as opposed to living in a busy apartment building. Most would definitely choose the former. However, with both options, it’s not as easy as all that. Dedicated servers cost […]
Nov 12, 2015
When it comes to choosing a server, you may have a number of features on your checklist. Every individual and company will have their own, unique needs. The good news is that, these days, just about everyone can find a solution that fits this distinct profile. That being said, uptime should always be at the […]
Nov 11, 2015
If you run a website, hopefully you already know what SEO (search engine optimization) is and why it matters. What you may not know, though, is the role servers play in where your page ranks in Google. Uptime The uptime of your site is directly influenced by your server. In fact, it’s the only factor […]
Nov 10, 2015
Every company these days has to be online. However, how we get online has changed a lot over the years. Two of the most important ways to host a business site are with dedicated servers and colocation. For help deciding which one makes the most sense for your company, let’s compare the two. Colocation Should […]
|
||||||||||||||||||||||||||||||||||||||||||||||||||